Chapter 16 : Service Chaining
Introduction :
What is service chaining
To be updated
How to do Service Chaining in OpenContrail:
Steps:
- Create 2 Network ( Left Network, Right Network)
- Create a VMs(VNFs eg: Firewall, NAT, etc) with Left, Right,
- Create a Service Template for each VNF (Fields: Name, version, Virtualization type, service mode, service type, interfaces)
- Create a Service Instance for each VNF (Fields: Name, Service template, Networks,Port tuples)
- Create a Network Policy (Allow traffic between Left and Right Networks, Select Service instances created )
- Apply the Network Policy in Left and Right Networks
Testing:
- Create a VM(VM1) in Left Network
- Create a VM(VM2) in Right Network
- Initiate a traffic from VM1 to VM2.
- The traffic will go via the Service Chain VM(Firewall). we can login to the Firewall VM(Service Insntace) and sniff the traffic or see the firewall logs.
Exercise 1:
Create a Firewall VNF, Router VNF.
VM1 traffic should go via Firewall VNF to reach VM2. vice versa.
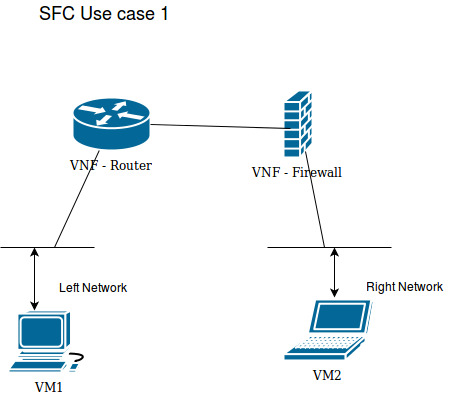
Step1:
Create 2 Networks named left,right in opentstack.
Left : 10.1.1.0/24
Right : 10.2.2.0/24
neutron net-create Left
neutron subnet-create Left 10.1.1.0/24 --name LeftS
neutron net-create Right
neutron subnet-create Left 10.2.2.0/24 --name RightS
Step2:
Create a 2 VMs (VNF) with Left,Right
Flavor - Ubuntu 14.04.5, RAM - 1G, Core -1
Cloudinit - Script to bring the second interface up, and enable IP forward. This script is part of the nova boot commad "user-data".
Bootscript.sh
#!/bin/bash
echo $'auto eth1\niface eth1 inet dhcp' | sudo tee /etc/network/interfaces.d/eth1.cfg > /dev/null
sudo ifup eth1
echo $'auto eth2\niface eth2 inet dhcp' | sudo tee /etc/network/interfaces.d/eth2.cfg > /dev/null
sudo ifup eth2
sudo sysctl net.ipv4.ip_forward net.ipv4.ip_forward=1
nova boot routerVNF --flavor 6 --image ubuntu14 --key-name testkey --security-groups default --user-data bootscript.sh --nic net-id=ab580d57-97d8-4b28-8800-42403b406609 --nic net-id=91eaa294-a5bc-4f9b-8dde-b8deeebb10bb
nova boot fwVNF --flavor 6 --image ubuntu14 --key-name testkey --security-groups default --user-data bootscript.sh --nic net-id=ab580d57-97d8-4b28-8800-42403b406609 --nic net-id=91eaa294-a5bc-4f9b-8dde-b8deeebb10bb
Step3:
Create a Service Template (use contrail UI)
FW Service Tempalte
Service Templates -> create ->
Name: FW
Version : v2
Virtualization Type : Virtual Machine
Service Mode : In-Network
Service Type : Firewall
Interfaces : Left, Right
Router Service Template
same as above.
Step4:
Create a Service Instance
FW Service Instance:
Service Instace -> create ->
Name: FW-SI
Service Template : FW
Interface Type: Left : Virtual Network : Left
Interface Type : Right Virtual Network : Right
PortTuples -> Tuple -> Left - 10.1.1.4, Right - 10.2.2.4
Router Service Instace:
Same as above
Step5:
Create a Network Policy
Policies -> New
Name : LeftToRight
Policy Rules:
Action: PASS, Protocol : ANY, Source : Left, Ports : Any, Destination: Right, Ports : Any,
Services : Yes
Service Instances : FW-SI, Router-SI
Step 6:
Apply the network Policy
Networks -> Edit Left Network
Network Policies : LeftToRight
Networks -> Edit Right Network
Network Policies : LeftToRight
Step 7:
Create a Source VM in the Left Network
Create a Destination VM in the Right Network
Ping from Source VM to Destination VM
Capture the traffic in FW-VNF VM and Router-VNF VM.
References:
http://www.opencontrail.org/port-tuples-service-chain-redundancy/